Summary
Students apply the design process to the problem of hiding a message in a digital image using steganographic methods, a PictureEdit Java class, and API (provided as an attachment). They identify the problems and limitations associated with this task, brainstorm solutions, select a solution, and implement it. Once their messages are hidden, classmates attempt to decipher them. Based on the outcome of the testing phase, students refine and improve their solutions.Engineering Connection
Software engineers follow the engineering design process to develop solutions (software applications) that accomplish tasks or solve problems. Software engineers also analyze data using a range of creative techniques to discover patterns and relationships. Modern steganography is the art or science of hiding data (messages) inside of digital files. This means that software engineers perform analyses that create and identify these hidden messages. In examples dealing with terrorism communication, their success or failure to identify messages can determine the outcome of an attack and citizen safety.
Learning Objectives
After this activity, students should be able to:
- Create a digital document with a hidden message.
- Apply the design process to solve a problem.
- Discover a message hidden using steganography.
Educational Standards
Each TeachEngineering lesson or activity is correlated to one or more K-12 science,
technology, engineering or math (STEM) educational standards.
All 100,000+ K-12 STEM standards covered in TeachEngineering are collected, maintained and packaged by the Achievement Standards Network (ASN),
a project of D2L (www.achievementstandards.org).
In the ASN, standards are hierarchically structured: first by source; e.g., by state; within source by type; e.g., science or mathematics;
within type by subtype, then by grade, etc.
Each TeachEngineering lesson or activity is correlated to one or more K-12 science, technology, engineering or math (STEM) educational standards.
All 100,000+ K-12 STEM standards covered in TeachEngineering are collected, maintained and packaged by the Achievement Standards Network (ASN), a project of D2L (www.achievementstandards.org).
In the ASN, standards are hierarchically structured: first by source; e.g., by state; within source by type; e.g., science or mathematics; within type by subtype, then by grade, etc.
NGSS: Next Generation Science Standards - Science
| NGSS Performance Expectation | ||
|---|---|---|
|
HS-ETS1-2. Design a solution to a complex real-world problem by breaking it down into smaller, more manageable problems that can be solved through engineering. (Grades 9 - 12) Do you agree with this alignment? |
||
| Click to view other curriculum aligned to this Performance Expectation | ||
| This activity focuses on the following Three Dimensional Learning aspects of NGSS: | ||
| Science & Engineering Practices | Disciplinary Core Ideas | Crosscutting Concepts |
| Design a solution to a complex real-world problem, based on scientific knowledge, student-generated sources of evidence, prioritized criteria, and tradeoff considerations. Alignment agreement: | Criteria may need to be broken down into simpler ones that can be approached systematically, and decisions about the priority of certain criteria over others (trade-offs) may be needed. Alignment agreement: | |
| NGSS Performance Expectation | ||
|---|---|---|
|
HS-ETS1-4. Use a computer simulation to model the impact of proposed solutions to a complex real-world problem with numerous criteria and constraints on interactions within and between systems relevant to the problem. (Grades 9 - 12) Do you agree with this alignment? |
||
| Click to view other curriculum aligned to this Performance Expectation | ||
| This activity focuses on the following Three Dimensional Learning aspects of NGSS: | ||
| Science & Engineering Practices | Disciplinary Core Ideas | Crosscutting Concepts |
| Use mathematical models and/or computer simulations to predict the effects of a design solution on systems and/or the interactions between systems. Alignment agreement: | Both physical models and computers can be used in various ways to aid in the engineering design process. Computers are useful for a variety of purposes, such as running simulations to test different ways of solving a problem or to see which one is most efficient or economical; and in making a persuasive presentation to a client about how a given design will meet his or her needs. Alignment agreement: | Models (e.g., physical, mathematical, computer models) can be used to simulate systems and interactions—including energy, matter, and information flows—within and between systems at different scales. Alignment agreement: |
International Technology and Engineering Educators Association - Technology
-
Identify the design problem to solve and decide whether or not to address it.
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Optimize a design by addressing desired qualities within criteria and constraints.
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Develop a plan that incorporates knowledge from science, mathematics, and other disciplines to design or improve a technological product or system.
(Grades
9 -
12)
More Details
Do you agree with this alignment?
State Standards
National Council of Teachers of Mathematics - Math
-
Understand numbers, ways of representing numbers, relationships among numbers, and number systems
(Grades
Pre-K -
12)
More Details
Do you agree with this alignment?
Nebraska - Science
-
Propose designs and choose between alternative solutions of a problem
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Implement the selected solution
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Communicate the problem, process, and solution
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Recognize creativity, imagination, and a good knowledge base are all needed to advance the work of science and engineering
(Grades
9 -
12)
More Details
Do you agree with this alignment?
Materials List
Each group needs a computer with:
- Java installed, such as Eclipse, NetBeans, Java_Editor, JCreator or Jedi
- image editing tools to enable the opening of image files, such as Microsoft Windows, Paint, Adobe Photoshop or similar application
- Picture Edit Zip, a zip folder that contains necessary files for the activity
Worksheets and Attachments
Visit [www.teachengineering.org/activities/view/uno_plainsight_lesson01_activity1?fdfb4aec8cba479aee19cd446127e7] to print or download.Pre-Req Knowledge
Students and teachers should have a working knowledge of steganography and steganographic methods, which can be acquired while completing the associated lesson, Hidden in Plain Sight or through research on the topic.
In addition, the activity is meant to be part of the AP Computer Science curriculum. Knowledge of the Java programming language is required.
Introduction/Motivation


In this activity, you will apply the design process to create a hidden message in a digital image using a steganographic technique. Steganography has been used historically to convey secret messages in plain sight. The first known use of steganography was in ancient Greece, and it has been used in many wars since. In recent years, terrorists have used steganography to pass information and help plot attacks. Thus, computer software engineers are on the front lines for detecting messages hidden using steganography.
Figure 1 shows an example of an image hidden inside of another image using steganography. In Figure 1, the innocuous looking trees are hiding the cat, shown in Figure 2. The hidden image is revealed by removing all but the two least significant bits of each color component and then performing normalization on the resulting image.
In this activity, you will be both the creator of a hidden message and the attempted detector of a hidden message using steganography.
Procedure
Background
This activity is appropriate in an Advanced Placement (AP) Computer Science class using the Java programming language. It is an extension of what is taught in the AP curriculum and requires knowledge of Java programming.
The focus of the activity is teaching the engineering design process by using the concept of steganography. Using the resources provided in the attachments, students create an image with information hidden in it using steganography. To accomplish this task, they must follow the engineering design process, shown in Figure 3. They must identify the problem and its constraints, create ideas about how to modify the image, select and implement the solution, test the solution (done by classmates to see if they can discover the message), and finally refine the solution to better solve the problem.
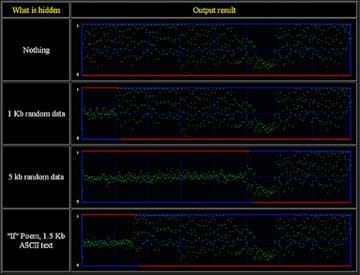
The engineering challenge is to use steganography to hide information in a provided image. The image, available software, and their knowledge of steganography are the constraints. The implementation is done using the Java PictureEdit class to modify the image in some fashion determined by the student.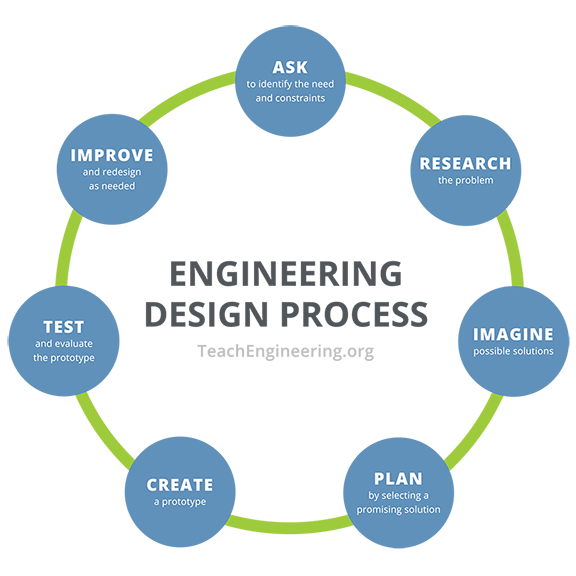
Refer to the Activity Example for example results from this activity, with explanations of the methods used.
Before the Activity
- Secure a computer lab for student use.
- Make sure the computers have Java installed as well as image editing tools.
- The PictureEdit class and API are in an attached zip file. Place these files on each computer along with the Java editor of your choice. The PictureEdit class must be in the same folder as your current Java files. Picture Edit Zip contains: PictureEdit.java and Picture Edit API documentation. Using the API documentation, you can see how the PictureEdit class is created and how you can modify images using it.
With the Students
- Divide the class into groups of two or three students each.
- Give students the PictureEdit class and API (Application Programming Interface) to use to edit image data for encryption and decryption (these files are included in the zip file). Using the API documentation (from whatever Java editor you are using), students can see how the PictureEdit class is created and how they can modify images using it.
- Using the PictureEdit class, students open, modify and save image data to create their own methods of hiding information in an image file. Possible methodology choices include:
- least significant bit modification
- chaffing and winnowing
- bit-plane complexity segmentation steganography
- transform domain methods
- Fourier series (for music)
Additionally, students can attempt to create their own method to hide information in the file.
- Regardless of the method chosen, students should be able to speak to its positive and negative features.
- Once information has been hidden successfully, have student groups exchange final products with other groups for testing.
- The testing phase has two parts:
- First, once each group has received another group's final product (a message hidden using steganography), they should search for the message and method of encoding. If the message/method is not determined after an allotted amount of time, the original group should share/explain its method of message encoding.
- Second, if the group detects the message and the method, they should share/describe to the first group how fast and/or easily they found the message with the hidden information.
- To conclude the activity, hold a class discussion in which students share their experiences and lessons learned with hiding messages and attempting to discover hidden messages.
- Finally, have students present how they applied the design process in the creation of their projects. Require that this take the form of a lab write-up that includes what the student group did in each step of the engineering design process.
Vocabulary/Definitions
application programming interface (API): A protocol intended to be used as an interface by software components to communicate with each other.
steganography: A method for concealing information within seemingly innocent media.
Assessment
Pre-Activity Assessment
Questions: Have students discuss or write answers to the following prompts.
- Describe what you know about the engineering design/software design process. (Answer: It is a cyclical process that is followed to accomplish a task or goal. It requires several steps including: analysis of the problem, design of a solution, implementation of the design, testing of the design, and possible extensions of the design.)
- How can you apply a design process to solving a problem? (The design process is basically a problem solving process. After identifying the specific problem you want to address, you must develop some possible solutions and implement them. Finally, you must adequately test your implementation to see if it functions correctly.)
Activity Embedded Assessment
Observations: Observe student progress and check in with each group throughout course of the activity Have each student group submit a copy of their final product. As students present to the class about their experience, assess students based on their understanding of the concepts of steganography.
Post-Activity Assessment
Writing: Have students answer the following writing prompt:
- Explain how you applied the design process in your creation of a hidden message using steganographic techniques. (Example answer: First, we had to define/identify the problem and its scope/constraints. In our project, this was to hide a message within an image. We had to determine what type of image to use and the size of the image. We had to decide on what type of message to send (image or text) and select a steganographic method to use. Next, we designed a solution to the problem and implemented it using the Java class that was provided as a resource. Classmates who attempted to decipher the hidden message tested our solution and gave us feedback on how difficult it was to discover. Finally, we considered ways to improve the way we hid the message in an image.)
Performance: Have students complete the following performance assessment. Refer to the Activity Examples for ideas.
- Select another image and hide a message in it using a different steganographic technique. Detail how you used the steps of the design process in developing your solution.
Troubleshooting Tips
The PictureEdit class must be located in the same folder as the Java files being used.
Subscribe
Get the inside scoop on all things TeachEngineering such as new site features, curriculum updates, video releases, and more by signing up for our newsletter!More Curriculum Like This
hrough this lesson, students experience a portion of the engineering design process as they research steganography and steganographic methods; identify problems, criteria and constraints; brainstorm possible solutions; and generate ideas.
Copyright
© 2013 by Regents of the University of Colorado; original © 2013 Board of Regents, University of NebraskaContributors
Derek Babb, Brian SandallSupporting Program
IMPART RET Program, College of Information Science & Technology, University of Nebraska-OmahaAcknowledgements
The contents of this digital library curriculum were developed as a part of the RET in Engineering and Computer Science Site on Infusing Mobile Platform Applied Research into Teaching (IMPART) Program at the University of Nebraska-Omaha under National Science Foundation RET grant number CNS 1201136. However, these contents do not necessarily represent the policies of the National Science Foundation, and you should not assume endorsement by the federal government.
Last modified: August 30, 2020






User Comments & Tips