Quick Look
Grade Level: 9 (9-12)
Time Required: 1 hours 45 minutes
(two 50-minute sessions)
Expendable Cost/Group: US $0.00
Group Size: 1
Activity Dependency: None
Subject Areas: Computer Science, Problem Solving, Reasoning and Proof, Science and Technology
NGSS Performance Expectations:
| HS-ETS1-2 |

Summary
Students become red team ethical hackers by building a safe hacking lab and learning tools used to test real networks. Students are introduced to ethical hacking, containers, network engineering, wordlist generation, and brute-force password cracking. Using Podman, students create and network their hacker system (Kali Linux) and target system (Metasploitable2 or “Meta2”). With Netcat, they scan the target’s IPs, ports, and services, then design efficient username and password lists with Maskprocessor. Finally, students test vulnerabilities by attempting controlled brute-force attacks on the target and its DVWA web server using Medusa and their custom wordlists. The activity builds practical lab skills and broadens understanding of computer science topics such as cryptography, web apps, networking, containers, and AI/LLMs.Engineering Connection
Red team ethical hackers use a shorter version of the engineering design process to test the security of computer systems. They start by gathering information, then they try to break into the system through penetration testing, and finally they report what they find. This is a lot like what engineers do when they check and test their designs to make sure they work safely. In fact, ethical hacking is considered the "verification and validation" part of network and security engineering, which means hackers make sure systems do what they are supposed to and find weak spots before real attackers do. Ethical hacking is another way engineers solve problems and protect important technology.
Learning Objectives
After this activity, students should be able to:
- Understand how to detect system network vulnerabilities.
- Develop customized wordlists to crack both usernames and passwords.
- Explain the connection between usernames, passwords, and hash protocols (md5, sha1, sha256).
- Ethically hack into a system and web server with brute force and crack both usernames and passwords.
- Discuss solutions to secure systems from threat actors.
- Use and contrast AI/LLM system outputs for bash scripting and coding.
Educational Standards
Each Teach Engineering lesson or activity is correlated to one or more K-12 science,
technology, engineering or math (STEM) educational standards.
All 100,000+ K-12 STEM standards covered in Teach Engineering are collected, maintained and packaged by the Achievement Standards Network (ASN),
a project of D2L (www.achievementstandards.org).
In the ASN, standards are hierarchically structured: first by source; e.g., by state; within source by type; e.g., science or mathematics;
within type by subtype, then by grade, etc.
Each Teach Engineering lesson or activity is correlated to one or more K-12 science, technology, engineering or math (STEM) educational standards.
All 100,000+ K-12 STEM standards covered in Teach Engineering are collected, maintained and packaged by the Achievement Standards Network (ASN), a project of D2L (www.achievementstandards.org).
In the ASN, standards are hierarchically structured: first by source; e.g., by state; within source by type; e.g., science or mathematics; within type by subtype, then by grade, etc.
NGSS: Next Generation Science Standards - Science
| NGSS Performance Expectation | ||
|---|---|---|
|
HS-ETS1-2. Design a solution to a complex real-world problem by breaking it down into smaller, more manageable problems that can be solved through engineering. (Grades 9 - 12) Do you agree with this alignment? |
||
| Click to view other curriculum aligned to this Performance Expectation | ||
| This activity focuses on the following Three Dimensional Learning aspects of NGSS: | ||
| Science & Engineering Practices | Disciplinary Core Ideas | Crosscutting Concepts |
| Design a solution to a complex real-world problem, based on scientific knowledge, student-generated sources of evidence, prioritized criteria, and tradeoff considerations. Alignment agreement: | Criteria may need to be broken down into simpler ones that can be approached systematically, and decisions about the priority of certain criteria over others (trade-offs) may be needed. Alignment agreement: | |
Common Core State Standards - Math
-
Build new functions from existing functions
(Grades
9 -
12)
More Details
Do you agree with this alignment?
State Standards
Nevada - Technology
-
Research and Information Fluency: Students apply digital tools to gather, evaluate, and use information.
(Grades
K -
12)
More Details
Do you agree with this alignment?
-
Technology Operations and Concepts: Students demonstrate a sound understanding of technology concepts, systems, and operations.
(Grades
K -
12)
More Details
Do you agree with this alignment?
Materials List
Each student needs:
- 1 networked (internet) Microsoft Windows 10/11 computer (minimum 4 GB RAM, 128 GB drive)
- Podman Desktop from https://podman-desktop.io/downloads
- Kali Linux and Metasploitable2 images (containers)
- Kali Linux binaries (Net-tools, Plocate, Netcat, Metasploit Framework, wordlists, Lynx, Maskprocessor (mp64), and Medusa)
Worksheets and Attachments
Visit [www.teachengineering.org/activities/view/uon-2999-ethical-hacking-lab-podman-activity] to print or download.Pre-Req Knowledge
Student prerequisite knowledge requirements:
- Basic understanding and navigation of Windows and Linux operating systems, including Windows Powershell and Linux Terminal
- Basic understanding of the Linux Advanced Package Tool and how to perform updates
- Basic understanding of and ability to access Linux binaries help or manual pages
- Basic understanding of local area networks (LAN) and the seven layers of the OSI Model
- Basic understanding of IP addresses, subnets, system ports, and services
- Basic understanding of hash (password) cracking and cryptography
- Basic understanding of how to query information from AI/LLMs
Introduction/Motivation
Today, we are kicking off an exciting, hands-on activity on ethical hacking. Who knows what “red-team hacking” is? (Let students offer answers.) Red-team hacking is when a group of trusted computer experts is given permission to act like “the bad guys” and try to break into a company’s computers or buildings, or trick people with fake emails. They do this to test how strong the company’s defenses really are. It is different from a normal “penetration test” because it can involve more than just computers—it might also check how well people notice tricks, or how fast the company’s security team reacts. Everything is done with permission and clear rules, and the main goal is to help the company find weaknesses and fix them before real hackers can exploit them.
Let’s watch a video (1:38 minutes). While you watch, I want you to think about the following questions:
- What is password cracking?
- What are the two main ways to crack passwords?
- Threat actors usually do not attempt to log in to an unauthorized account directly; instead, they use what indirect methods?
- Are computing systems and web servers attacked using similar methods?
(Show the video to the class.)
So, let’s go over the questions posed previously.
- What is password cracking? (Answer: Process of trying to figure out or guess a password for a computer, system, network, or account, usually without permission.)
- What are the two main ways to crack passwords?
- Brute-force attack: This is when a program automatically tries every possible combination of letters, numbers, and symbols until it finds the correct one. It is very thorough but can take a long time.
- Dictionary attack: This method uses a list of common words, phrases, and previously leaked passwords (a "dictionary" or "wordlist") to try and guess the password. It is much faster than a brute-force attack if the password is a common word or phrase.
- Threat actors usually do not attempt to log in to an unauthorized account directly; instead, they use what indirect methods?
- Phishing: This involves sending fake emails or messages that trick people into revealing their passwords or other personal information. The messages often look like they are from a trusted company or service.
- Malware: This is malicious software that can be installed on a computer without the user's knowledge. It can record keystrokes, including passwords, and send them to the hacker.
- Data breaches: Threat actors do not always need to crack a password one by one. They often buy or find large databases of usernames and passwords that were stolen from a company's servers in a data breach. They then use these stolen credentials to try and log in to other accounts the person might have, a practice known as credential stuffing.
- Are computing systems and web servers attacked using similar methods? (Answer: Yes, many methods are similar because both rely on weaknesses such as weak passwords, unpatched software, misconfigured systems, or vulnerable services, though web servers may also face attacks specific to web applications, such as SQL injection or cross-site scripting.)
Now I want you to go to this website: Have I Been Pwned (https://haveibeenpwned.com) and enter your email address. (Give students time to enter their email addresses.) What did you find out? (Let students report their findings on whether their email and/or accounts have been compromised in the past five years [incident] and, if so, the degree of the compromise[s].)
Today you are going to be asked to build your own ethical hacking lab using Podman to learn the basics of password threats and vulnerabilities. Then you will apply what you have learned to create custom wordlists and brute-force/wordlist crack a system’s and a web server’s (“DVWA”) usernames and passwords.
Procedure
Background:
Red-team hacking is an authorized security exercise where trained professionals imitate real hackers to test an organization’s defenses. Unlike a basic penetration test, which mainly looks for technical flaws, red teaming can involve cyberattacks, social engineering, and even physical break-ins to see how well both technology and people respond. These exercises are done under strict rules of engagement and with full permission, and the purpose is not to cause harm but rather to uncover security weaknesses so the organization can resolve them before a real attacker tries to exploit them.
Podman containers, not to be confused with virtual machines, are process configurations that rely on a host operating system (OS). In the case of running Podman Desktop on Windows, users typically install the Windows Subsystem for Linux (WSL v2), which consists of a bare bones Linux OS (Fedora) that serves as the container(s) host system on which they run. Docker may also be configured to run Windows containers, which would utilize the host system’s OS but also open your Windows system up to a plethora of security vulnerabilities.

Podman Desktop provides a graphical user interface (GUI) management window that enables users to pull images and manage containers and applications. The Podman Desktop installation also prompts the user to install the Podman engine on which the container processes operate.
Before the Activity
- Optional: Make copies of the Pre/Post Assessment Worksheets. (1 per student)
- Provide digital or hard copies of the five Independent Practice Worksheets (see Attachments). (1 per student)
With the Students
Note: The four sections below need to be taught in sequential order!
Section 1: Engineer and network a Docker ethical hacking lab using containers (Kali, Metasploitable2)
- Optional: Have students complete the Pre Assessment Worksheet.
- Introduce Podman containers to the students:
- Podman containers, not to be confused with virtual machines, are process configurations that rely on a host OS. In the case of running Podman Desktop on Windows, users typically install the Windows Subsystem for Linux (WSL v2), which consists of a bare bones Linux OS (Fedora) that serves as the container(s) host system on which they run. Docker may also be configured to run Windows containers, which would utilize the host system’s OS but also open your Windows system up to a plethora of security vulnerabilities.
- Podman Desktop provides a GUI management window that enables users to pull images and manage containers and applications. The Podman Desktop installation also prompts the user to install the Podman engine on which the container processes operate.
- Let’s assume for this activity that we are going to stick with Linux containers and utilize WSL 2 within the Windows environment.
- Instruct students to open their computers.
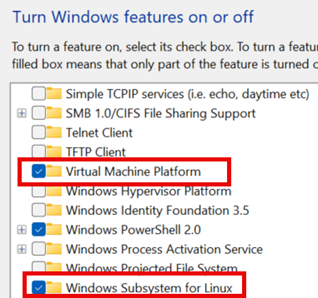
- Have students turn on two Windows Features: (a) Virtual Machine Platform and (b) Windows Subsystem for Linux. (See image below or Step 1.1 in the Teacher Guide.)
A screenshot of the "Turn Windows features on or off" menu, showing the checkboxes for "Virtual Machine Platform" and "Windows Subsystem for Linux" both selected.
- Have students restart their computers.
- Instruct students to update WSL and set to version 2 in PowerShell or Command Prompt (admin) by typing the following:
> wsl.exe --update
> wsl --set-default-version 2
- Have students do a status check to confirm everything is fine:
> wsl –status
- Lead students to Install Podman Desktop and Docker Engine
- Students can find the Podman Desktop downloads at https://podman-desktop.io/downloads.
- Remind students that we are interested in Podman Desktop for Windows (x64). (They should be automatically prompted to install the Podman Engine.)
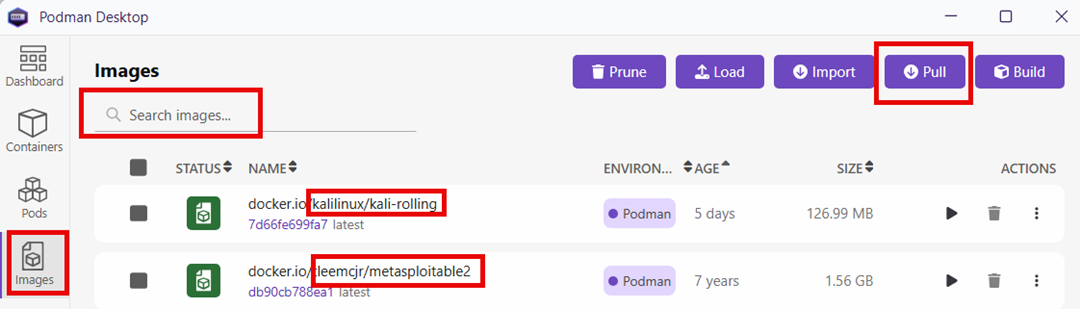
- In Podman Desktop, have students select Images in the left menu and Pull in the top menu. Search for and pull the following images: kalilinux/kali-rolling, tleemcjr/metasploitable2.
- Have students open a PowerShell terminal as administrator.
- In the first terminal, have them create their network to be shared by the containers and assign an IP range and subnet. (Note: In this example, the author created a network called “podnetwork” using bridge mode to host and an IP range beginning at 4.3.2.0 on /27 [cidr notation] or subnet 255.255.224.0.)
- After creation, check to make sure “podnetwork” is listed following the PowerShell command > podman network list. (See Step 1.4 in the Teacher Guide.)
- Tell students that it is best before running the sudo (super user do) command to enable “sudo” in Windows - Developer Settings. It is best practice to enable sudo when using it and disable it when not in use. Have students enable sudo. (See Step 1.5 in the Teacher Guide.)
- Have students open two PowerShell terminals and separately run both containers on the hackwork network. (The commands can be found in Step 1.5 in the Teacher Guide.)
- Once ready, students should have two terminal windows open to each of the containers’ file systems: (See Step 1.5 in the Teacher Guide.)
- Walk students through updating, upgrading, and installing the requisite Kali Linux binaries:
- At the Kali terminal, students should be logged in as root and see a # symbol prompt.
- Students should install the necessary binaries using the Advanced Packet Tool (APT):
- Update and upgrade
# apt update
# apt full-upgrade -y
- Install plocate (locate command) and update the database
# apt install -y plocate
# updatedb
- Students should test the locate command by locating the binary for Lynx. (See Step 1.6 in the Teacher Guide.)
- Have students install Kali Net-tools, Cewl, and Medusa:
# apt install -y net-tools
# apt install -y netcat
# apt install -y wordlists
# apt install -y maskprocessor (hint: use “mp64” to run from terminal)
# apt install -y lynx
# apt install -y medusa
# apt install -y hydra
- Have students install Netcat (IP and Port Scanning): # apt install -y netcat-traditional
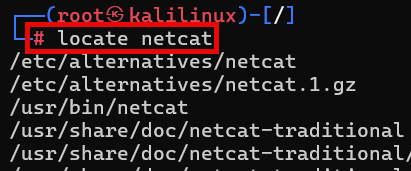
- Have students run the locate command to make sure Net-tools, Netcat, Lynx, Wordlists, Maskprocessor, and Medusa are installed. The image below shows an example using the locate function to search for instances of Netcat. Note: The “bin” in the Linux file path /usr/bin/netcat stands for “binary,” which are scripts or applications.
- Give each student a digital or hard copy of Section 1: Independent Practice Worksheet.
- Give students time for independent practice by providing this scenario (Section 1: Independent Practice Worksheet): The core binary used in Kali for targeting exploits in systems is called Metasploit (Framework). Your task is to research how to install Metasploit on Kali. Then use your Kali PowerShell terminal to install Metasploit and its database. Finish by starting up Metasploit and providing a screenshot of the graphic, version, and the msf6 > prompt with a search result for the vsftpd exploit.
- For the teacher: See Section 1: Independent Practice Worksheet Answer Key for a suggested solution.
- Have students finish the worksheet.
Section 2: Network Reconnaissance and Assessing Target Vulnerabilities
- Introduce Section 2 to the students by reading the following aloud:
“Our podnetwork uses the IP range 4.3.2.0/27. What that means is that both Kali and Metasploitable2 were assigned IP addresses on a first-come, first-served basis via the Domain Host Control Protocol (DHCP). Think of an IP address as like a key to joining a network. The /27 part is CIDR notation for the subnet 255.255.224.0. Subnets are a means toward creating local area networks (LANs). A router usually sits at the heart of a LAN and is the instrument that assigns new devices IP addresses via DHCP.”

A good tool for looking up CIDR notation is Subnet Ninja’s Cheat Sheet: https://subnet.ninja/subnet-cheat-sheet
There is a networking model known as the OSI 7 layers of networking. It breaks down the networking layers into seven groups to help with understanding. Routers, LANs, and IP addresses fall under Layer 3 (Network). See https://www.geeksforgeeks.org/open-systems-interconnection-model-osi.
Systems that are assigned IP addresses on a LAN communicate with one another via ports and services. Firewalls are used to manage open and closed ports and allow/disallow traffic.
For this guided practice, we are going to use Netcat to analyze and output a list of the target system’s open ports and services.
- Instruct students to look up the Kali and Metasploitable2’s IP addresses with ifconfig in separate PowerShell terminals. (See image below or Section 2.1 in the Teacher Guide.)
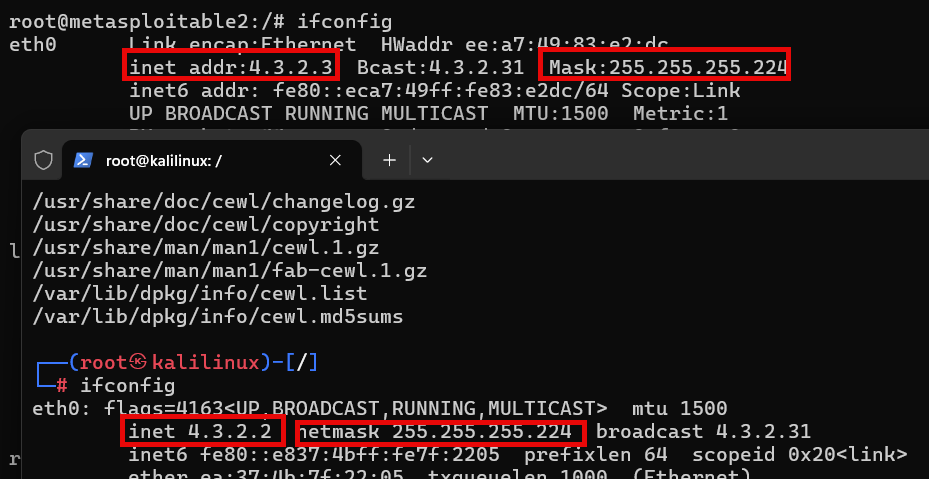
- Point out the following to the students: “We can see that both Kali and Metasploitable2 have been assigned IP addresses from the 4.3.2.0/27 range we specified when we created our ‘podnetwork’. That is good. We are going to focus on the target Metasploitable2’s IP address of 4.3.2.3.”
- Have students run Netcat against the target system’s IP 4.3.2.3 and ports 1 through 443, using the arguments -z (report connection status) and -v (verbose output). (See Section 2.2 in the Teacher Guide.)
- Tell students that they are going to focus on the Secure Shell (SSH) service “open” on port 22.
Port 22/tcp ssh (Secure Shell)
- Remind students that services like “ssh” listen for like connections from other hosts.
- Instruct students to connect to the target system via SSH port 22. (Note: At the conclusion of this activity, they will utilize the same service/port to password crack with Medusa.)
- Have students use their Kali terminal to install SSH and connect to the target system. (See Section 2.3 in the Teacher Guide.)
- Instruct students to connect to the target from Kali using SSH, the administrative user “msfadmin” and the ssh-rsa algorithm override for Kali to communicate to the target system.
- Remind students that the -l argument is for entering the username.
- Give students the rest of the class period to independently practice using the Section 2: Independent Practice Worksheet with the following hint: We’ll pretend that we don’t know the exact username and password for the Maskprocessor wordlists part of the activity; however, we’ll use the knowledge gained that both the username and password of the target system are eight characters in length and use the letters (a, d, f, I, m, n, s).
Section 3: Build Strategic User and Password Lists with Maskprocessor
- Introduce Maskprocessor to the students: “Maskprocessor (“mp64”) is a powerful Kali Linux tool to install. This open-source tool is used for creating custom wordlists from scanned websites. Wordlists are giant delimited lists of username and/or password possibilities.”

With Maskprocessor, users may generate custom wordlists based on criteria such as character sets, length, patterns, and combinations. Maskprocessor wordlists may be used with password cracking tools such as Hashcat, Hydra, Medusa, and John the Ripper. The more accurate your wordlist, the less time it takes to crack passwords.
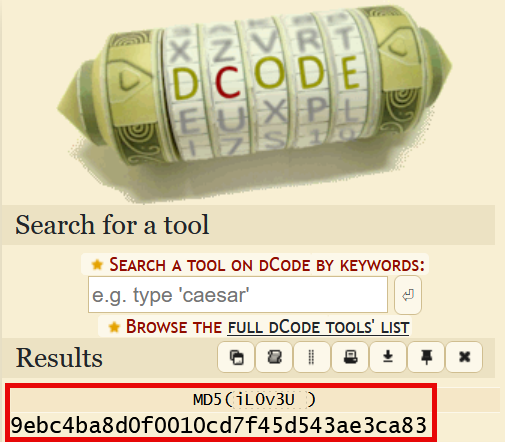
Of note is that at the heart of password cracking lies hashes. Hashes are strings of random-looking characters that are generated by a system to mask the original username or password. This process of masking is called a cipher. For example, a password such as “iL0v3U” will not be visible in the system to a threat actor. What will be available upon deep inspection is the hash generated from the password iL0v3U.
You can use a converter tool such as dCode (https://www.dcode.fr/hash-function) to play around with hashes like md5 and sha1. The following image is an example output of the password iL0v3U hashed with md5.
- Have students check to see if Maskprocessor is installed on the system.
- Use help to learn some Maskprocessor syntax with help (-h).
- Practice using the syntax with this example:
- Generate a wordlist that is three characters using only lower-case alpha (a – z).
- Output the wordlist to mp64_wordlist3.txt.
- Show the first and last five words generated in the wordlist using head and tail functions.
- Use the chmod command to change the file permissions to 775 (Read, Write).
- List the folder contents.
- Have students create a wordlist directory in Kali (/root/wordlists), change its permissions recursively, and generate three sample wordlists with Maskprocessor.
- Have students then create a wordlist directory and change its permissions to 775. The -R stands for recursive, meaning that the 775 directory permissions flow down to all the directories and files therein.
- Walk through Example 1 in Step 3.3 of the Teacher Guide.
- Walk through Example 2 in Step 3.3 of the Teacher Guide.
- Give students time to independently practice using the Section 3: Independent Practice Worksheet.
Section 4: Exploit Target System Vulnerability and Brute-Force Crack with Medusa
- Introduce Medusa to the students: “Medusa is an amazing password cracking tool available for Kali Linux. It is a parallel, modular, brute-force login username and password cracker that supports numerous protocols for target entry to commence its attack. See: https://www.kali.org/tools/medusa.”
- For a list of the Medusa function’s arguments (options), have students open their Kali PowerShell terminal and type in: # medusa -h.
- Have students do this example as a class: “If we were to type in a Medusa command to brute-force attack a target’s usernames and passwords, we would use the following commands:
# medusa -h [target IP] -U [username list] -P [password list] -M [module] -t [threads default 16]”
- Give students time to independently practice using the Section 4: Independent Practice Worksheet.
Section 5: Exploit Target System’s Web Server (“DVWA”) Vulnerability and Brute-Force Crack with Hydra
- Introduce Hydra to the students: “Hydra is a parallel, multi-threaded brute-force username and password cracking tool. Hydra configured to be able to crack website login pages (username and password input fields). However, let’s first get acquainted with the text-based Linux web browser Lynx. The Lynx browser will prove useful when using either Docker or Podman to build and work with your container-based ethical hacking lab.
- Have students verify the install of Lynx performed earlier in the lesson: # apt install -y lynx
- Instruct students to open the Damn Vulnerable Web Application (“DVWA”) that comes packaged with Metasploitable2. See image below.
![A screenshot of a Linux terminal window. The title bar says root@kali-linux:~/wordlists. The main text on the screen, written in large ASCII art, spells out "metasploitable". Below it, a warning states: "Warning: Never expose this VM to an untrusted network!" and provides a contact email. A red rectangular box highlights the text "Login with msfadmin/msfadmin to get started". Below this, another red box surrounds a list of five options: "TWiki", "phpMyAdmin", "Mutillidae", "DVWA", and "WebDAV". At the very bottom, a third red box highlights a blue command bar with instructions on how to navigate the interface using arrow keys and other commands. The text in the command bar is "Commands: Use arrow keys to move, '?' for help, 'q' to quit, '<-' to go back. Arrow keys: Up and Down to move. Right to follow a link; Left to go back. H)elp O)ptions P)rint G)o M)ain screen Q)uit /=search [delete]=history list". A screenshot of a Linux terminal window. The title bar says root@kali-linux:~/wordlists. The main text on the screen, written in large ASCII art, spells out "metasploitable". Below it, a warning states: "Warning: Never expose this VM to an untrusted network!" and provides a contact email. A red rectangular box highlights the text "Login with msfadmin/msfadmin to get started". Below this, another red box surrounds a list of five options: "TWiki", "phpMyAdmin", "Mutillidae", "DVWA", and "WebDAV". At the very bottom, a third red box highlights a blue command bar with instructions on how to navigate the interface using arrow keys and other commands. The text in the command bar is "Commands: Use arrow keys to move, '?' for help, 'q' to quit, '<-' to go back. Arrow keys: Up and Down to move. Right to follow a link; Left to go back. H)elp O)ptions P)rint G)o M)ain screen Q)uit /=search [delete]=history list".](/content/uon_/activities/uon-2999-ethical-hacking/uon-2999-ethical-hacking-image9.png)
- Point out the following to students: “Now we can see above the DVWA comes packaged with TWiki, phpMyAdmin, Mutillidae, DVWA, and WebDAV. The admin username and password “msfadmin” is also provided, but we will ignore that for now. The Commands at bottom utilize the arrow keys to move and lowercase and uppercase letters and symbols for menu options.”
- Have students use the arrow keys to highlight “DVWA” and surf to that page.
- Have students notice the Username and Password entry fields and a Login option. Please ignore the supplied admin username and password.
- Give students time to independently practice using the Section 5: Independent Practice Worksheet.
- Optional: Have students complete the Post Assessment Worksheet.
Vocabulary/Definitions
Advanced Package Tool (APT): The main command-line package manager for Debian (Kali Linux) and its derivatives.
Artificial Intelligence (AI): Refers to the development of computer systems that can perform tasks that typically require human intelligence, such as learning, problem-solving, decision-making, and perception.
Classless Inter-Domain Routing (CIDR) notation: A compact representation of an IP address and its network mask.
Google Gemini: An AI language learning model based chatbot.
Grok 3: An AI language learning model based chatbot.
Hydra: A parallelized network login and password cracker that supports multiple protocols.
IP address: A unique identifying number in the form of four octets assigned to every device connected to a network.
Kali Linux: A Debian-based Linux distribution built for cybersecurity (red, blue team).
Language learning models (LLMs): Often called large language models (LLMs), these are AI systems trained on vast datasets of text to understand, generate, and manipulate human language. They power applications such as chatbots, translation tools, and text summarizers.
Linux root: The name or account that by default has administrative access to all commands and files on a Linux or Unix operating system.
Linux sudo: Short for “superuser do,” it elevates a user’s privileges to execute admin-level commands.
Linux terminal: A text-based interface that allows users to interact with the system by entering commands and utilizing functions and arguments, managing files, and controlling system processes.
local area network (LAN): A computer network that often serves as an internet gateway, connecting devices in a limited area, usually managed by a layer three router (IP addresses, subnet).
Lynx: The standard for Linux text-based web browsers.
Maskprocessor (mp64): An open-source custom wordlist generator that allows the specification of a standard character set or any set of characters to be used in generating the wordlists.
Medusa : A parallel brute-force login and password cracker that supports multiple protocols.
Metasploit Framework: A framework of malware and delivery tools used to gain access and hack targets.
OSI Layer 3: The network layer that provides a means of transferring data packets from a source to a destination host via one or more networks.
Podman containers: Not virtual machines, but purpose-built applications that share a virtual Linux kernel.
Podman Desktop: A computer network that often serves as an internet gateway, connecting devices in a limited area, usually managed by a Layer 3 router (IP addresses, subnet).
subnet: A logical division of an IP network.
Windows PowerShell: A cross-platform, text-based task automation solution made of a command-line shell, a scripting language, and a configuration management framework. It runs on Windows, Linux, and macOS.
Windows Subsystem for Linux (WSL2): A feature of Windows that makes it possible to run a Linux environment on a Windows machine, without the need for a separate virtual machine or dual booting.
Assessment
Pre-Activity Assessment
Pre-Assessment Worksheet: The Pre/Post Assessment will be given to the students at the onset of instruction.
Activity Embedded (Formative) Assessment
Independent Practice Sessions: Each of the four stages requires students to complete an independent practice assignment (Engineer/Build the Ethical Hacking Lab with Docker [Kali, Metasploitable2], Network Reconnaissance, Design and Build Wordlists, and Brute-Force Username and Password Crack) to practice new skills. Teachers use the answer keys to compare student answers with suggested methods. However, students may discover or utilize different methods to solve the problems.
Post-Activity (Summative) Assessment
Post-Assessment Worksheet: The Post-Activity Assessment is the same as Pre/Post Assessment and is used to gauge student learning and the effectiveness of both the activity and the instruction.
Safety Issues
Not applicable other than acceptable use of the computing resources by students.
Troubleshooting Tips
Troubleshooting issues is a crucial part of this multi-step lesson, given its heavy reliance on technology, systems, and binaries. Take care to go slowly and methodically through each instructional step, making SURE that each student is on track and has not been left behind.
Windows 10/11 help and the Linux manual pages are helpful resources.
What happens if Windows is restarted or booted?
- To start Podman and containers on Windows, first open Podman and click on the run symbol next to each container.
- Then open two PowerShell terminals as administrator on Windows and enter the commands in Step 1.5 in the Teacher Guide.
Activity Extensions
- Students may be asked to refine their wordlists (smaller, faster processing times).
- Students may be asked to change their Medusa or Hydra port/service/protocol attack vector and note their findings.
- Students may be asked to perform network and vulnerability scanning with tools other than Netcat.
Activity Scaling
The activity may be made less difficult for middle school students by increasing the number of provided (ordered) username/password characters of the target system before generating the wordlists.
The activity may be made more difficult for high school students by decreasing or eliminating the provided username/password characters of the target system before generating the wordlists.
Additional Multimedia Support
- Teachers may present the material using the Guided + Independent docs attached OR develop the content into PowerPoint or Google Slides.
Subscribe
Get the inside scoop on all things Teach Engineering such as new site features, curriculum updates, video releases, and more by signing up for our newsletter!More Curriculum Like This
This activity provides a foundation for ethical hacking by using tools in Kali Linux to analyze and attack a target system, Metasploitable2. Students learn about ethical hacking, containers, and network engineering as they use Docker to build and connect their own hacker and target systems. They ide...
References
Podman Support, Podman Desktop, 2025, Podman
https://podman.io
Podman Support, dockerhub tleemcjr/metasploitable2, 2016, Docker, Inc
https://hub.docker.com/r/tleemcjr/metasploitable2
Podman Support, dockerhub kalilinux/kali-rolling (weekly snapshot), 2025, Docker, Inc.
https://hub.docker.com/r/kalilinux/kali-rolling
Subnet Ninja, Subnet Cheat Sheet, 2025, Subnet Ninja, Inc.
https://subnet.ninja/subnet-cheat-sheet
dCode, dCode Cipher Identifier, 2025, dCode
https://www.dcode.fr/cipher-identifier
GeeksforGeeks, Open Systems Interconnection Model (OSI), 2023, Sanchhaya Education Private Limited
https://www.geeksforgeeks.org/open-systems-interconnection-model-osi
Rapid7, Metasploitable 2, 2025, Rapid7, Inc.
https://docs.rapid7.com/metasploit/metasploitable-2
Kali Tools, Netcat, 2025, OffSec Services Limited
https://www.kali.org/tools/netcat
Kali Tools, Maskprocessor, 2025, OffSec Services Limited
https://www.kali.org/tools/maskprocessor
Kali Tools, Medusa, 2025, OffSec Services Limited
https://www.kali.org/tools/medusa
Kali Tools, Net-tools, 2025, OffSec Services Limited
https://www.kali.org/tools/net-tools
Kali Tools, Wordlists, 2025, OffSec Services Limited
https://www.kali.org/tools/wordlists
Kali Tools, Plocate, 2025, OffSec Services Limited
https://www.kali.org/tools/plocate
Copyright
© 2025 by Regents of the University of Colorado; original © 2025 University of Nevada RenoContributors
Frankie ClarkSupporting Program
Research Experience for Teachers (RET), Research Experience in Cybersecurity for Nevada Teachers (RECNT), University Of NevadaAcknowledgements
This activity was developed under the National Science Foundation RET grant number 2302187. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of the National Science Foundation.
Many thanks for the guidance and support of Prof. Jay Thom and Executive Director Shamik Sengupta, Cybersecurity Center, University of Nevada Reno.
Last modified: September 29, 2025



User Comments & Tips