Quick Look

Summary
This activity provides a foundation for ethical hacking by using tools in Kali Linux to analyze and attack a target system, Metasploitable2. Students learn about ethical hacking, containers, and network engineering as they use Docker to build and connect their own hacker and target systems. They identify and install necessary tools on Kali Linux, including Nmap to scan the target for open ports and running processes. This information helps them create efficient username and password lists, or "dictionaries," using Crunch. The activity culminates with students using Hydra to brute-force crack the target system's passwords with their custom wordlists.Engineering Connection
Ethical hacking applies a systematic, disciplined, and quantifiable approach to solving problems and designing solutions. It is a form of reverse engineering for cybersecurity and the verification and validation branch of network and security engineering. Instead of building a system, ethical hackers deconstruct it to find flaws and use that knowledge to design stronger defenses.
Learning Objectives
After this activity, students should be able to:
- Understand how to detect system network vulnerabilities.
- Develop customized wordlists to crack both usernames and passwords.
- Explain the connection between usernames, passwords, and hash protocols (md5, sha1, sha256).
- Ethically hack into a system and brute-force crack both usernames and passwords.
- Discuss solutions to secure systems from threat actors.
Educational Standards
Each Teach Engineering lesson or activity is correlated to one or more K-12 science,
technology, engineering or math (STEM) educational standards.
All 100,000+ K-12 STEM standards covered in Teach Engineering are collected, maintained and packaged by the Achievement Standards Network (ASN),
a project of D2L (www.achievementstandards.org).
In the ASN, standards are hierarchically structured: first by source; e.g., by state; within source by type; e.g., science or mathematics;
within type by subtype, then by grade, etc.
Each Teach Engineering lesson or activity is correlated to one or more K-12 science, technology, engineering or math (STEM) educational standards.
All 100,000+ K-12 STEM standards covered in Teach Engineering are collected, maintained and packaged by the Achievement Standards Network (ASN), a project of D2L (www.achievementstandards.org).
In the ASN, standards are hierarchically structured: first by source; e.g., by state; within source by type; e.g., science or mathematics; within type by subtype, then by grade, etc.
NGSS: Next Generation Science Standards - Science
| NGSS Performance Expectation | ||
|---|---|---|
|
HS-ETS1-2. Design a solution to a complex real-world problem by breaking it down into smaller, more manageable problems that can be solved through engineering. (Grades 9 - 12) Do you agree with this alignment? |
||
| Click to view other curriculum aligned to this Performance Expectation | ||
| This activity focuses on the following Three Dimensional Learning aspects of NGSS: | ||
| Science & Engineering Practices | Disciplinary Core Ideas | Crosscutting Concepts |
| Design a solution to a complex real-world problem, based on scientific knowledge, student-generated sources of evidence, prioritized criteria, and tradeoff considerations. Alignment agreement: | Criteria may need to be broken down into simpler ones that can be approached systematically, and decisions about the priority of certain criteria over others (trade-offs) may be needed. Alignment agreement: | |
| NGSS Performance Expectation | ||
|---|---|---|
|
HS-ETS1-4. Use a computer simulation to model the impact of proposed solutions to a complex real-world problem with numerous criteria and constraints on interactions within and between systems relevant to the problem. (Grades 9 - 12) Do you agree with this alignment? |
||
| Click to view other curriculum aligned to this Performance Expectation | ||
| This activity focuses on the following Three Dimensional Learning aspects of NGSS: | ||
| Science & Engineering Practices | Disciplinary Core Ideas | Crosscutting Concepts |
| Use mathematical models and/or computer simulations to predict the effects of a design solution on systems and/or the interactions between systems. Alignment agreement: | Both physical models and computers can be used in various ways to aid in the engineering design process. Computers are useful for a variety of purposes, such as running simulations to test different ways of solving a problem or to see which one is most efficient or economical; and in making a persuasive presentation to a client about how a given design will meet his or her needs. Alignment agreement: | Models (e.g., physical, mathematical, computer models) can be used to simulate systems and interactions—including energy, matter, and information flows—within and between systems at different scales. Alignment agreement: |
Common Core State Standards - Math
-
Build new functions from existing functions
(Grades
9 -
12)
More Details
Do you agree with this alignment?
International Technology and Engineering Educators Association - Technology
-
Optimize a design by addressing desired qualities within criteria and constraints.
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Determine the best approach by evaluating the purpose of the design.
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Synthesize data and analyze trends to make decisions about technological products, systems, or processes.
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Diagnose a flawed system embedded within a larger technological, social, or environmental system.
(Grades
9 -
12)
More Details
Do you agree with this alignment?
-
Analyze the stability of a technological system and how it is influenced by all the components in the system, especially those in the feedback loop.
(Grades
9 -
12)
More Details
Do you agree with this alignment?
State Standards
Nevada - Technology
-
Research and Information Fluency: Students apply digital tools to gather, evaluate, and use information.
(Grades
K -
12)
More Details
Do you agree with this alignment?
-
Critical Thinking, Problem Solving, and Decision Making: Students use critical thinking skills to plan and conduct research, manage projects, solve problems, and make informed decisions using appropriate digital tools and resources.
(Grades
K -
12)
More Details
Do you agree with this alignment?
-
Digital Citizenship: Students understand human, cultural, and societal issues related to technology and practice legal and ethical behavior.
(Grades
K -
12)
More Details
Do you agree with this alignment?
Materials List
Students will need the following lesson materials:
- 1 networked (internet) Microsoft Windows 10/11 computer (minimum 4 GB RAM, 128 GB drive)
- Docker Desktop downloaded from https://docs.docker.com/desktop
- Kali Linux and Metasploitable2 images (containers)
Worksheets and Attachments
Visit [www.teachengineering.org/activities/view/uon-2997-ethical-hacking-lab-activity] to print or download.Pre-Req Knowledge
Student prerequisite knowledge requirements:
- Basic understanding and navigation of the Windows operating system
- Basic understanding and navigation of the Linux operating system
- Basic understanding and navigation of both Windows PowerShell and Linux terminal
- Basic understanding of the Linux Advanced Package Tool and how to perform updates
- Basic understanding of and ability to access Linux binaries help or manual pages
- Basic understanding of local area networks (LAN) and the OSI Seven Layers
- Basic understanding of IP addresses, subnets, system ports, and services
- Basic understanding of hash (password) cracking and cryptography
Introduction/Motivation
Today, we're kicking off an exciting, hands-on activity on ethical hacking. I know the word "hacking" can sound a little intimidating or even a bit nefarious, but we're going to explore it from the perspective of a cybersecurity professional. Our goal is to think like a hacker so we can learn how to protect computer systems and data. This is a huge field in cybersecurity, and it's a skill set that's in high demand.
Let’s watch a video called: What is Password Cracking? While you watch it, I want you to think about the following questions:
- What is password cracking?
- What are the two main ways to crack passwords?
- What indirect methods do threat actors use to attempt to log in to an unauthorized account instead of trying to log in directly?
(Show the video: https://youtu.be/gSlopIz-tJ8?si=HM5jeIJewtVlRhK6 [1:38 minutes] to the class.)
So, let’s go over your answers to the questions posed previously.
- What is password cracking? (Answer: The process of trying to figure out a password for a computer, network, or account, usually without permission.)
- What are the two main ways to crack passwords? Answers:
- Brute-force attack: This is when a program automatically tries every possible combination of letters, numbers, and symbols until it finds the correct one. It's very thorough but can take a long time.
- Dictionary attack: This method uses a list of common words, phrases, and previously leaked passwords (a "dictionary" or "wordlist") to try and guess the password. It's much faster than a brute-force attack if the password is a common word or phrase.
- What indirect methods do threat actors use to attempt to log in to an unauthorized account instead of trying to log in directly? Answers:
- Phishing: This involves sending fake emails or messages that trick people into revealing their passwords or other personal information. The messages often look like they're from a trusted company or service.
- Malware: This is malicious software that can be installed on a computer without the user's knowledge. It can record keystrokes, including passwords, and send them to the hacker.
- Data breaches: Threat actors don't always need to crack a password one by one. They often buy or find large databases of usernames and passwords that were stolen from a company's servers in a data breach. They then use these stolen credentials to try and log in to other accounts the person might have, a practice known as credential stuffing.
Now I want you to go to this website: Have I Been Pwned (https://haveibeenpwned.com) and enter your email address. (Give students time to enter their email addresses.) What did you find out? (Let students report their findings on whether their email and/or accounts have been compromised in the past five years [incident] and the degree of the compromise[s].)
In this activity, you are going to be asked to build your own ethical hacking lab to learn threat and vulnerability basics and apply what you’ve learned to create custom wordlists and brute-force/wordlist crack a system’s usernames and passwords. Let’s get started!
Procedure
Background
Ethical hacking (or penetration testing) is an authorized security practice where professionals, known as ethical hackers or "white hats," simulate cyberattacks against an organization's systems to find and fix vulnerabilities before malicious actors can exploit them. This process is distinct from illegal hacking because it operates under strict rules of engagement and with full permission from the system owner. The goal is to provide a comprehensive security assessment by testing everything from technical flaws in network infrastructure to human susceptibility to social engineering, ultimately strengthening the target's defenses.
Kali Linux is a powerful, specialized operating system specifically designed for penetration testing and ethical hacking. Kali Linux comes preloaded with hundreds of essential security tools, ranging from information gathering utilities to actual exploit frameworks. In this activity, the Kali Linux container serves as the attacker system, providing the environment from which students will launch network reconnaissance scans, generate password lists, and execute brute-force attacks against the target machine.
Metasploitable2 is an intentionally built, vulnerable virtual machine (VM) or container image, created for the express purpose of training in cybersecurity. It is not a system one would ever run on a production network; instead, it is configured with numerous well-known security weaknesses, flawed services, and deliberately weak passwords. In this lab, the Metasploitable2 container serves as the safe target system, allowing students to practice common cyberattacks, such as exploiting open ports and guessing login credentials, in a controlled, legal, and isolated environment.
Network reconnaissance is the initial phase of any attack, whether ethical or malicious, where the attacker gathers information about a target network and its systems. This is analogous to a spy scouting a location before an operation, and it is crucial for creating a successful attack strategy. Tools such as Nmap are used to perform tasks such as port scanning, which reveals active devices, the operating systems they run, and, most important, which services and ports (such as SSH, FTP, or Telnet) are open and potentially vulnerable to attack.
Wordlist generation is the strategic creation of customized text files, known as dictionaries or wordlists, that contain a large number of potential passwords and usernames. Tools such as Crunch allow users to define criteria such as minimum and maximum length, character sets (e.g., mixing letters, numbers, and symbols), and specific patterns, making the resulting list highly targeted. This process is designed to optimize brute-force attacks by narrowing down the vast space of possible passwords to a more manageable and context-relevant set, thereby reducing the time needed to crack a password.
Brute-force cracking is a method of obtaining login credentials by systematically trying a large number of username and password combinations until the correct one is found. Tools like Hydra are employed for this task because they can automate the process, rapidly testing combinations from a pre-generated wordlist against various network services and protocols (e.g., FTP, Telnet, SSH). While effective, the efficiency of a brute-force attack is heavily dependent on the quality of the wordlist and the computing power available, as the process can be time-consuming if the password is long and complex.
Before the Activity
- Optional: Make copies of the Pre/Post Assessment (2 per student).
With the Students
Day1
Section 1 - Engineer and network a Docker ethical hacking lab using containers (Kali, Metasploitable2)
- Optional: Have students complete the Pre/Post Assessment.
- Define Docker containers and Docker for the students:
- Docker containers, not to be confused with virtual machines, are process configurations that rely on a host OS. In the case of running Docker Desktop on Windows, users typically install the Windows Subsystem for Linux (WSL v2), which consists of a bare bones Linux OS (Ubuntu) that serves as the host system on which the containers run. Docker may also be configured to run Windows containers, which would utilize the host system’s OS but open the Windows system to a plethora of security vulnerabilities.

- Docker Desktop provides a graphical user interface (GUI) management window that enables users to pull images and manage containers and applications. The Docker desktop installation also prompts the user to install the Docker engine on which the container processes operate.
- Let’s assume for this activity that we’re going to stick with Linux containers and utilize WSL 2 within the Windows environment.
- Instruct students to open their computers.
- Have students turn on two Windows Features: (a) Virtual Machine Platform and (b) Windows Subsystem for Linux. (See Figure 2 or Step 1.1 in the Teacher Guide.)
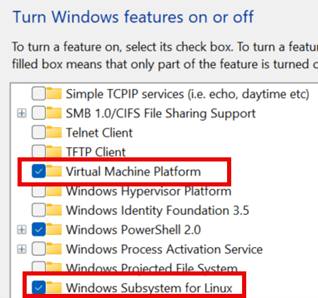
- Have students restart their computers.
- Instruct students to update WSL and set to version 2 in PowerShell or Command Prompt (admin) by typing the following:
> wsl.exe --update
> wsl --set-default-version 2
- Have students do a status check to confirm everything is fine:
> wsl –status
- Lead students to Install Docker Desktop and Docker Engine:
- Students can find the Docker Desktop downloads at https://docs.docker.com/desktop.
- Remind students that we are specifically interested in Docker Desktop for Windows – x86_64.
- After students click on the link or navigate to the link, they will be automatically prompted to install the Docker Engine.
- In Docker Desktop, have students select images in the left menu and search at the top to pull images kalilinux/kali-rolling AND tleemcjr/metasploitable2. (See Figure 3 or Step 1.3 in the Teacher Guide.)
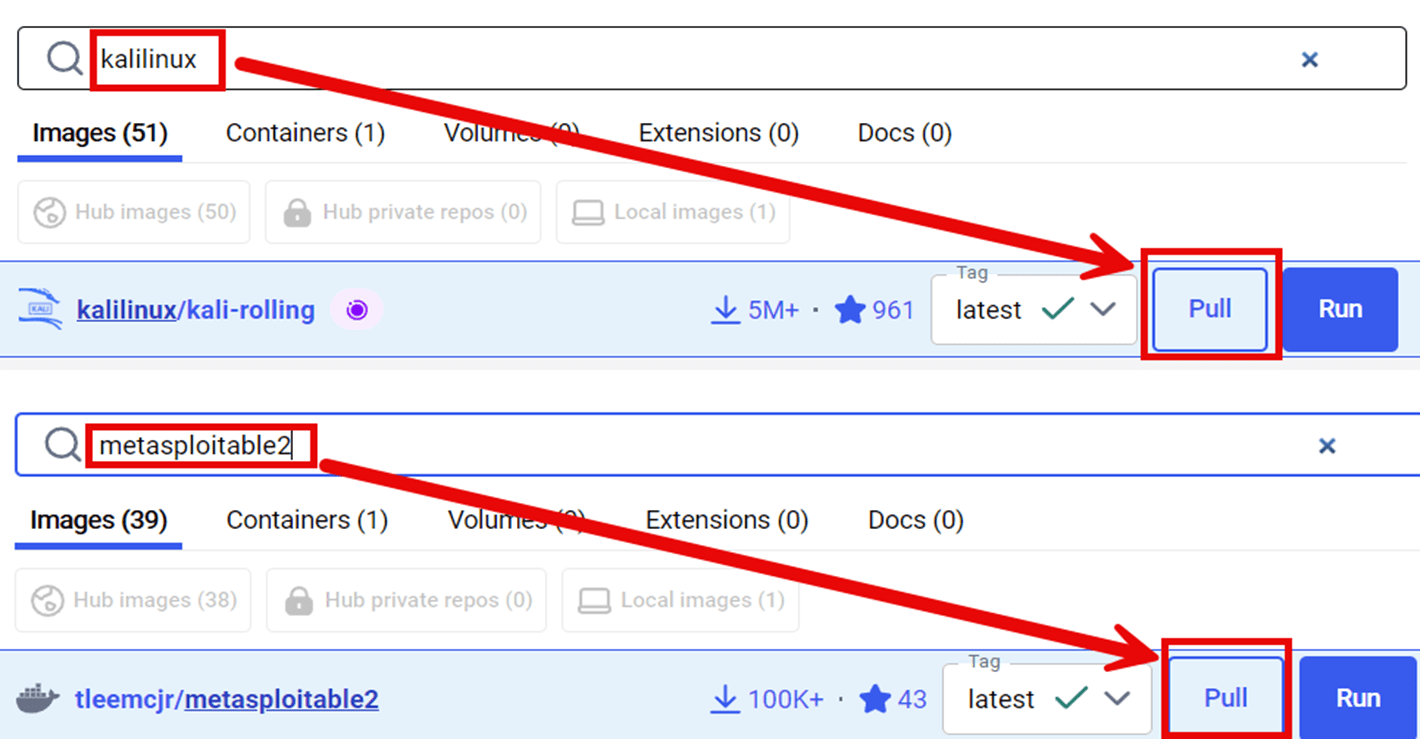
- Have students open a PowerShell terminal as administrator.
- In the first terminal, have them create their network to be shared by the containers and then assign an IP range and subnet. [Note: In this example, the author created a network called “hackwork” using bridge mode to host and an IP range beginning at 192.168.10.1 on /24 (CIDR notation) or subnet 255.255.255.0.]
- After creation, check to make sure the network, here “hackwork,” is listed following the PowerShell command > docker network list. (See Step 1.4 in the Teacher Guide.)
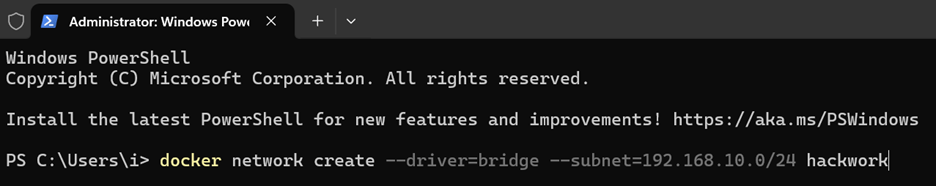
- After creating their network (here “hackwork”), have students check to make sure “hackwork” is listed following the PowerShell command > docker network list. (See Step 1.4 in the Teacher Guide.)
- Tell students that it’s best before running the sudo (super user do) command to enable “sudo” in Windows - Developer Settings. It’s best practice to enable sudo when using and disable it when not in use. Have students enable sudo. (See Step 1.5 in the Teacher Guide.)
- Have students open two PowerShell terminals and separately run both containers on the hackwork network. (The commands can be found in Step 1.5 in the Teacher Guide.)
- Once ready, students should have two terminal windows open to each of the containers’ file systems: (See Figure 5 or Step 1.5 in the Teacher Guide.)
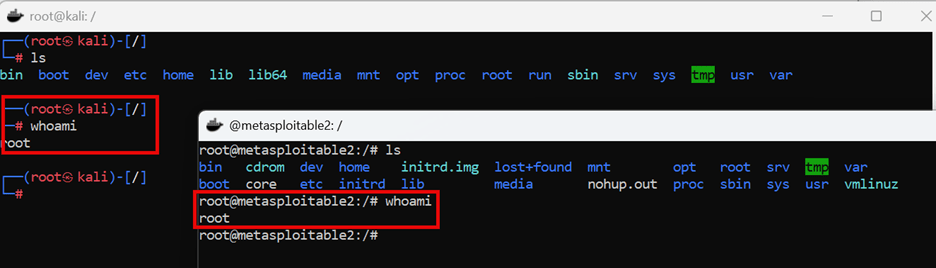
- Walk students through updating, upgrading and installing the requisite Kali Linux binaries:
- At the Kali terminal, students should be logged in as root and see a # symbol prompt.
- Students should install the necessary binaries using the Advanced Packet Tool (APT):
- Update and upgrade
# apt update
# apt full-upgrade -y
- Install plocate (locate command) and update the database
# apt install -y plocate
# updatedb
- Student should test the locate command by listing all /home locations: (See Step 1.6 in the Teacher Guide.)
- Students should then install Kali Net-tools, Nmap, Crunch, and Hydra.
# apt install -y net-tools
# apt install -y nmap
# apt install -y crunch
# apt install -y hydra
- Students should then run the locate command to make sure Net-tools, Nmap, Crunch, and Hydra are installed. (See Figure 6 or Step 1.6 in the Teacher Guide for an example with Crunch.) Note: The “bin” in the Linux file path /usr/bin/crunch stands for “binary,” which are scripts or applications.
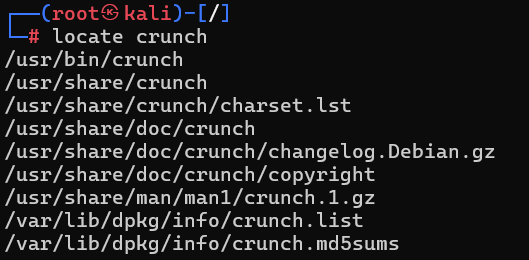
- Give students time for independent practice by providing this scenario (Section 1: Independent Practice Worksheet): The core binaries used in Kali for targeting exploits in systems are part of the Metasploit Framework suite of tools. Your task is to research how to install Metasploit on Kali. Then use your Kali PowerShell terminal to install Metasploit and its database. Finish by starting up Metasploit and providing a screenshot of the graphic, version, and the msf6 > prompt.
- For the teacher: See Section 1: Independent Practice Worksheet – Answer Key for a suggested solution.
Section 2 - Network Reconnaissance and Assessing Target Vulnerabilities
- Introduce Section 2 to the students by reading the following aloud:
“Our hackwork network uses the IP range of 192.168.10.0/24. What that means is that both Kali and Metasploitable2 were assigned IP addresses on a first-come, first-served basis via the Domain Host Control Protocol (DHCP). Think of an IP address as a key to joining a network. The /24 part is CIDR notation for the subnet 255.255.255.0. Subnets are a means of creating local area networks (LANs). A router usually sits at the heart of a LAN and is the instrument that assigns new devices IP addresses via DHCP.”

A good tool for looking up CIDR notation is Subnet Ninja’s Cheat Sheet: https://subnet.ninja/subnet-cheat-sheet.
There is a networking model known as the OSI 7 layers of networking. It breaks down the networking layers into seven groups to help with understanding. Routers, LANs, and IP addresses fall under layer three (Network). See: https://www.geeksforgeeks.org/open-systems-interconnection-model-osi.
Systems that are assigned IP addresses on a LAN communicate with one another via ports and services. Firewalls are used to manage open and closed ports and allow/disallow traffic.
For this guided practice, we are going to use Nmap to analyze and output a list of the target system’s open ports and services.
- Instruct students to look up the Kali and Metasploitable2’s IP addresses with ifconfig in separate PowerShell terminals. (See Figure 8 or Section 2.1 in the Teacher Guide.)
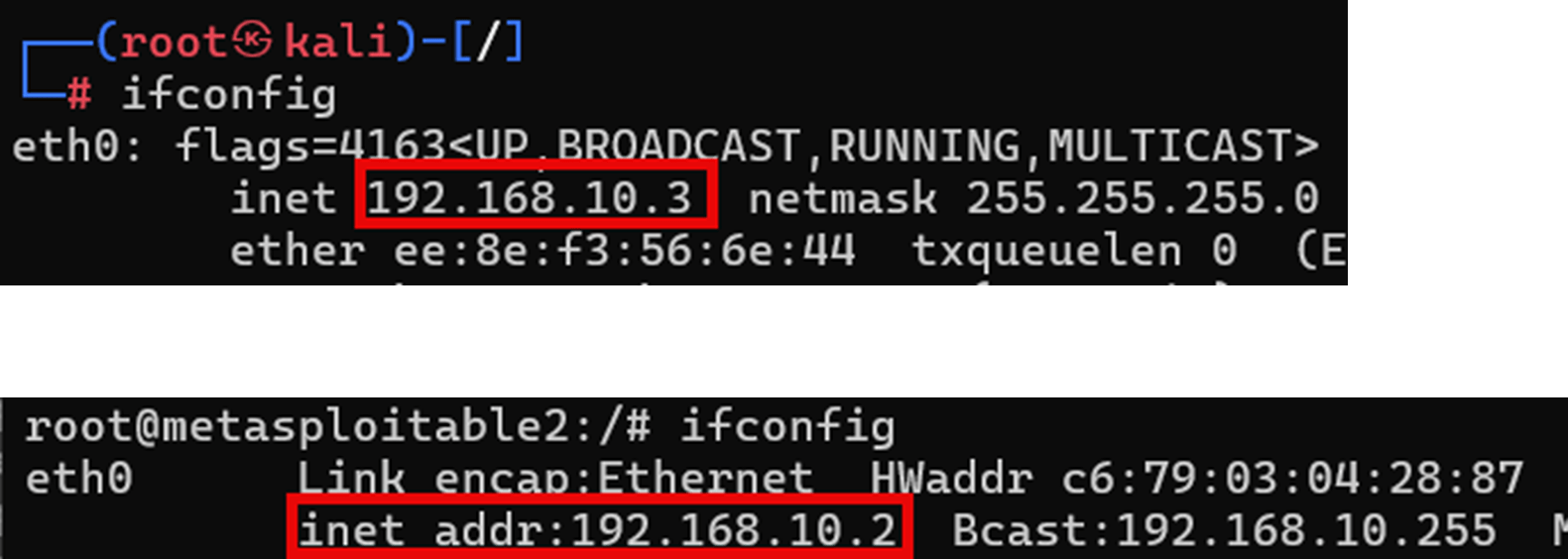
- Point out the following to the students: “We can see that both Kali and Metasploitable2 have been assigned IP addresses from the 192.168.10.0/24 range we specified when we created our “hackwork” network. That’s good. We are going to focus on the target Metasploitable2’s IP address of 192.168.10.2.”
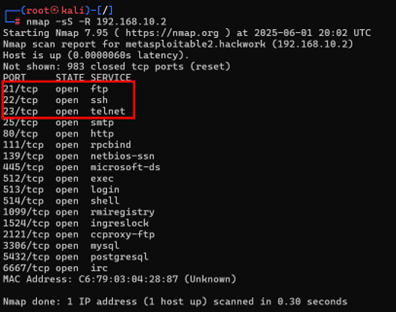
- Have students run Nmap against the target system’s IP, 92.168.10.2, using the arguments -sS (silent mode) and -R (reverse DNS lookup). (See Section 2.2 in the Teacher Guide.)
- Tell students that they are going to focus on the top three listed open ports and services:
- Port 21/tcp ftp (File Transfer Protocol)
- Port 22/tcp ssh (Secure Shell)
- Port 23/tcp telnet (Teletype Network)
- Remind students that services such as “ftp” and “ssh” listen for like connections from other hosts. The “tcp” stands for Transmission Control Protocol, which ensures that an error-checked delivery of all packets between applications running on hosts has occurred.
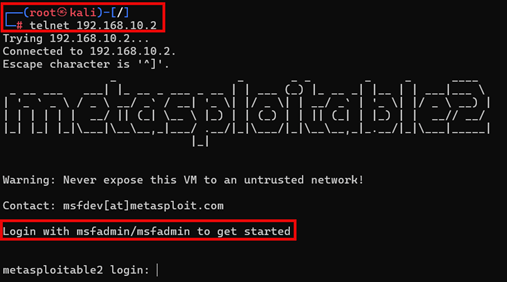
- Instruct students to use their Kali terminal to install telnet to connect to the target system.
- Have students note that the telnet service on Metasploitable2 is running on port 23 and it is simple to exploit it from Kali using a telnet connection string. (Note: The username and password “msfadmin” are listed in Figure 10.)
- Give students the rest of the class period to independently practice using the Section 2 Independent Practice Worksheet with the following hint: We’ll pretend that we don’t know the exact username and password for the Crunch wordlists part of the lesson; however, we’ll use the knowledge gained that both the username and password of the target system are eight characters in length and use the letters (a, d, f, I, m, n, s).
Day 2
Section 3 - Build Strategic User and Password Lists with Crunch
- Read the following script to introduce Crunch:
“A powerful Kali Linux tool to install is Crunch. The open-source tool Crunch is often used for creating custom wordlists (a.k.a. “dictionaries”). Wordlists are giant delimited lists of username and password possibilities. The most popular wordlist is “RockYou,” which is included in the Kali Linux Default metapackage. RockYou2024 has grown to more than 135 GB, containing more than 9 billion passwords!”

See: https://github.com/intelligencegroup-io/RockYou2024
With Crunch, users may generate custom wordlists based on criteria such as character sets, length, patterns, and combinations. Crunch wordlists may be used with password cracking tools like Hashcat, Hydra, Medusa, and John the Ripper. The more accurate you make your custom Crunch wordlist, the less time it takes to crack passwords.
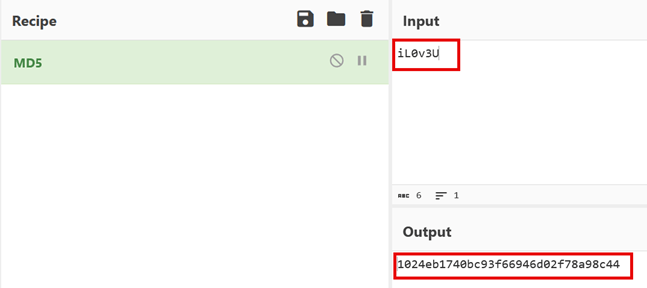
Of note is that at the heart of password cracking lies hashes. Hashes are strings of random-looking characters that are generated by a system to mask the original username or password. This process of masking is called a cipher. For example, a password such as “iL0v3U” will not be visible in the system to a threat actor. What will be available upon deep inspection is the hash generated from the password iL0v3U.
You can use a converter tool such as cyberchef.org to play around with hashes like md5 and sha1. (Display Figure 12 to the class as example output of the password iL0v3U hashed with md5.)
- Have students use the Kali PowerShell terminal to install Crunch: # apt install -y crunch
- Introduce the following basic Crunch syntax, character sets, wordlist output, and custom patterns to the class:
Basic Syntax:
The basic syntax for using Crunch is as follows:
crunch <min_length> <max_length> [options]
<min_length>: The minimum length of the generated words.
<max_length>: The maximum length of the generated words.
[options]: Additional options to customize the wordlist generation process.
Character Sets:
Crunch allows you to define custom character sets to include or exclude specific characters in the generated wordlists. Here are some commonly used character set options:
-t <character_set>: Specifies a custom character set to be used. For example, -t abc123 will generate words using the characters 'a', 'b', 'c', '1', '2', and '3'.
-f <file>: Specifies a file containing a list of characters to be used as a character set.
Wordlist Output:
Crunch provides options to control the output of the generated wordlist:
-o <output_file>: Specifies the output file where the generated wordlist will be saved.
-s <start_offset>: Sets the starting point for generating words. For example, -s 100 will start generating words from the 100th position.
-b <byte_offset>: Sets the maximum file size for the generated wordlist. For example, -b 1MB restricts the output file size to 1 megabyte.
Custom Patterns:
Crunch allows you to define custom patterns or masks to generate words that follow specific formats. Some pattern options include:
%: Specifies a lowercase character.
^: Specifies an uppercase character.
@: Specifies any character (lowercase, uppercase, or numeric).
*: Specifies any character (lowercase, uppercase, numeric, or special).
For example, to generate five-character words consisting of an uppercase letter followed by four lowercase letters, you can use the following command:
crunch 5 5 -t ^@@@@ -o output.txt
- Instruct students to create a wordlist directory in Kali (/root/wordlists) and generate three sample wordlists with Crunch. (See the Teacher Guide for examples.)
- Give students time to complete the Section 3 Independent Practice Worksheet.
Section 4 - Exploit Target System Vulnerability and Brute-Force Crack with Hydra
- Introduce Section 4 with the following: “Hydra is an amazing password-cracking tool available for Kali Linux. It is a parallelized login multithread-capable password cracker that supports numerous protocols for target entry to commence its attack.” (See: https://www.kali.org/tools/hydra.)
- Have students open their open your Kali PowerShell terminal and type # hydra -h for a list of Hydra’s arguments (options). (See Step 4.1 in the Teacher Guide.)
- Have students brute-force attack a target’s usernames and passwords by typing the following:
# hydra -L usernames.txt -P wordlist.txt <targetIP> <protocol>
- Give students time to complete the Section 4 Independent Practice Worksheet.
- Optional: Have students complete the Pre/Post Assessment.
Vocabulary/Definitions
Advanced Package Tool (APT): The main command-line package manager for Debian (Kali Linux) and its derivatives.
CIDR notation: A compact representation of an IP address and its network mask.
Crunch: A wordlist generator that allows users to specify a standard character set or any set of characters to be used in generating the wordlists.
Docker containers: Not virtual machines, but purpose-built applications that share a virtual Linux kernel.
Docker Desktop: An application that provides a graphical user interface (GUI) to build, share, and run containerized applications on a local machine.
Hydra: A parallelized network login and password cracker that supports multiple protocols.
IP address: A unique identifying number in the form of four octets assigned to every device connected to a network.
Kali Linux: A Debian-based Linux distribution built for cybersecurity (red, blue team).
Linux root: The name or account that by default has administrative access to all commands and files on a Linux or Unix operating system.
Linux sudo: Short for superuser do, a command-line utility that elevates a user’s privileges to execute admin-level commands.
Linux terminal: A text-based interface that allows users to interact with the system by entering commands and utilizing functions and arguments, managing files, and controlling system processes.
local area network (LAN): A computer network that often serves as an internet gateway connecting devices in a limited area, usually managed by a layer three router (IP addresses, subnet).
Metasploit Framework: A framework of malware and delivery tools to gain access and hack targets.
OSI Layer Three: The network layer that provides a means of transferring data packets from a source to a destination host via one or more networks.
subnet: A logical division of an IP network.
Windows PowerShell: A cross-platform, text-based task automation solution made of a command-line shell, a scripting language, and a configuration management framework. It runs on Windows, Linux, and macOS.
Windows Subsystem for Linux (WSL2): A feature of Microsoft Windows that users to run a Linux environment on a Windows machine, without the need for a separate virtual machine or dual booting.
Assessment
Pre-Activity Assessment
Pre-Activity Assessment: The Pre-Post Assessment will be given to the students at the onset of instruction, and teachers can use it to assess students’ pre-activity knowledge.
Activity Embedded (Formative) Assessment
Each of the four stages required to complete the assignment (Engineer/Build the Ethical Hacking Lab with Docker (Kali, Metasploitable2), Network Reconnaissance, Design and Build Wordlists, and Brute Force Username and Password Crack) have answer keys (attached). However, students may discover or utilize different methods to solve the problems. The answer keys are suggested methods.
Post-Activity (Summative) Assessment
Post-Activity Assessment: The Pre-Post Assessment is the same as the Pre-Assessment and is used to gauge student learning and the effectiveness of both the activity and instruction.
Safety Issues
Not applicable other than acceptable use of the computing resources by students (see Acceptable Use Policy).
Troubleshooting Tips
Troubleshooting issues is a crucial part of this multi-step lesson, given its heavy reliance on technology, systems, and binaries. Much care should be taken by the instructor to go slowly and methodically through each instructional step, making SURE that each student is on track and hasn’t been left behind.
Windows 10/11 Help and the Linux manual pages are great help resources.
Activity Extensions
- Students may be asked to refine their wordlists (smaller, faster processing times).
- Students may be asked to change their Hydra port/service/protocol attack vector and note their findings.
- Students may be asked to perform network and vulnerability scanning with tools other than Nmap.
Activity Scaling
- The activity may be made less difficult for middle school students by increasing the number of provided (ordered) username/password characters of the target system before generating the wordlists.
- The lesson may be made more difficult for high school students by decreasing or eliminating the provided username/password characters of the target system before generating the wordlists.
Additional Multimedia Support
- Teachers may present the material using the Guided + Independent docs attached OR develop the content into PowerPoint or Google Slides.
Subscribe
Get the inside scoop on all things Teach Engineering such as new site features, curriculum updates, video releases, and more by signing up for our newsletter!More Curriculum Like This
Students become red team ethical hackers by building a safe hacking lab and learning tools used to test real networks. Students are introduced to ethical hacking, containers, network engineering, wordlist generation, and brute-force password cracking. Using Podman, students create and network their ...
References
Docker Support, dockerdocs Docker Desktop, 2025, Docker Inc.
https://docs.docker.com/desktop
Docker Support, dockerdocs Install Docker Desktop on Windows, 2025, Docker, Inc.
https://docs.docker.com/desktop/setup/install/windows-install
Docker Support, dockerhub tleemcjr/metasploitable2, 2016, Docker, Inc
https://hub.docker.com/r/tleemcjr/metasploitable2
Docker Support, dockerhub kalilinux/kali-rolling (weekly snapshot), 2025, Docker, Inc.
https://hub.docker.com/r/kalilinux/kali-rolling
Subnet Ninja, Subnet Cheat Sheet, 2025, Subnet Ninja, Inc.
https://subnet.ninja/subnet-cheat-sheet
GeeksforGeeks, Open Systems Interconnection Model (OSI), 2023, Sanchhaya Education Private Limited
https://www.geeksforgeeks.org/open-systems-interconnection-model-osi
Rapid7, Metasploitable 2, 2025, Rapid7, Inc.
https://docs.rapid7.com/metasploit/metasploitable-2
Kali Tools, Nmap, 2025, OffSec Services Limited
https://www.kali.org/tools/nmap
Kali Tools, Crunch, 2025, OffSec Services Limited
https://www.kali.org/tools/crunch
Kali Tools, Hydra, 2025, OffSec Services Limited
https://www.kali.org/tools/hydra
Copyright
© 2025 by Regents of the University of Colorado; original © 2025 University of NevadaContributors
Frankie ClarkSupporting Program
Research Experience for Teachers (RET), Research Experience in Cybersecurity for Nevada Teachers (RECNT), University of NevadaAcknowledgements
This activity was developed under the National Science Foundation RET grant number 2302187. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of the National Science Foundation.
Many thanks for the guidance and support of Prof. Jay Thom and Executive Director Shamik Sengupta, Cybersecurity Center, University of Nevada Reno.
Last modified: November 20, 2025



User Comments & Tips